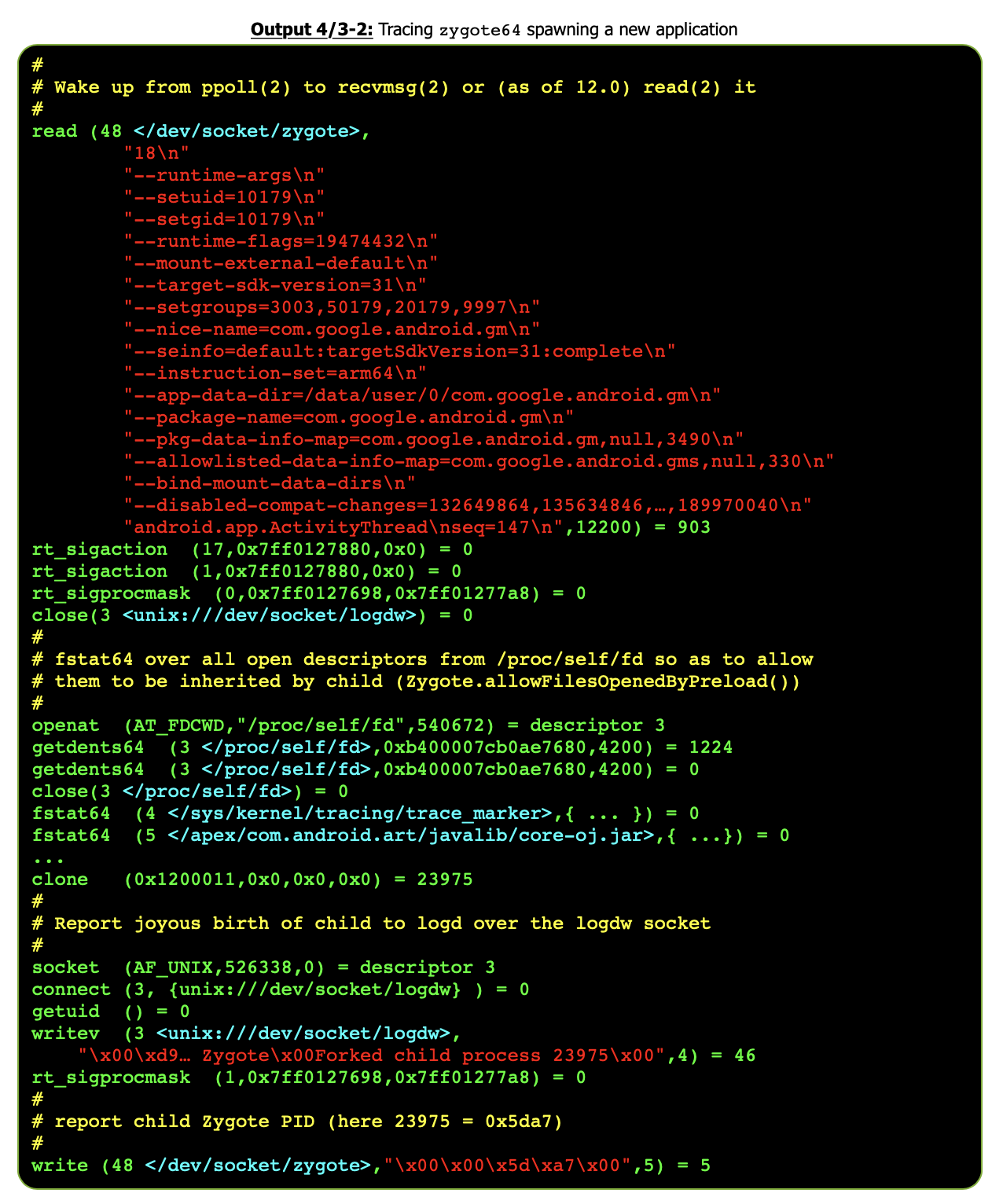
- Preface: (BTC is $59k, only a month and a half later.. :-)
- Chapter 1: Table 1/1-1 - Android versions, with %ages - updated to March 2021 (previous was Feb 2021, though mistakenly said May 2020)
- Chapter 2:
- Table 2/4-5 (Samsung Exynos devices) - Added NPU device
(Thanks to my good friend _@bazad who wrote about the Exynos NPU vulnerability before being taken by the spaceship)vertex10 drivers/vision/npu/npu-vertex.c NPU sr100 drivers/uwb/sr100.c S21 Ultra: Ultra Wide Band (UWB)
- Table 2/4-5 (Samsung Exynos devices) - Added NPU device
- Chapter 3:
- Table 3/4-1 - (Linux pseudo filesystems actively
used by Android 11) - Added BinderFS and filled in missing description for FunctionFS:
/dev/binderfs binderfsLinux 5.0+: Dynamic Binder devices (q.v. II/8) /dev/usb-ffs functionfsUSB functions (Gadget driver)
- Table 3/4-1 - (Linux pseudo filesystems actively
used by Android 11) - Added BinderFS and filled in missing description for FunctionFS:
- Chapter 4:
- Table 4/2-2 (Qualcomm /vendor/bin) - Added spdaemon which eluded me
because it's not used in Google devices..
spdaemon Secure Processing Unit (SPU) manager (on non-Google devices) - Table 4/2-5 (MTK /vendor/bin) - this was left woefully incomplete. Sorry
about that (versioning problem). Here's what it should look like:
… (will add this soon)
- Table 4/2-2 (Qualcomm /vendor/bin) - Added spdaemon which eluded me
because it's not used in Google devices..
- Chapter 8:
- Added
copy_per_lineinitdirective (new in 12.0), and that 'critical' (for services) now takes arguments - Table 8/7-1 (cont):
- Added snapuserd.rc under "System & Volume Management" right after snapshotctl.rc (which it apparently replaces)
- Filled cppreopts.rc in the table (I had omitted that, sorry)
cppreopts.rc Copy preoptimized files
- Added
- Update of Table 9/5-1 with
system_server_dumper - Added:
Android 12 adds the
before Figure 9/4-3system_server_dumperservice. As its name implies, this is adumpsysonly service with no clients, listing the properties ofSystemServer(start count and elapsed time),SystemServiceManager(started service classes) and theSystemServerInitThreadPool. - Added (Before Table 9/3-3, to expand on "dynamic" service lookup):
The client API of
a.os.ServiceManagerallows (as of Android 11.0) thewaitFor[Declared]Service(svcName)methods.
-
Table 10/3-6 had some missing fields. Here's all of it:
Table 10/3-6: The elements in /etc/sysconfig/ and/etc/permissions/ filesElement Meaning groupGlobal group IDs given to packages (III/2) permissionBuilt-in UID to permission mappings (III/2) assign-permissionAssign namepermission touid(III/2)split-permissionSplit namepermission fortargetSdkversion (III/2)libraryBuilt-in shared libraries [unavailable-]featureIndicate or hide a platform feature (for <uses-feature>)allow-in-power-save[-except-idle]Allow packageto operate even device is in different power modesallow-in-data-usage-saveallow-unthrottled-locationAllow continuous location updates allow-ignore-location-settingsOverride location settings allow-implicit-broadcastExempt broadcast from 8.0 background delivery restrictions app-linkAndroid application link (II/3) system-user-[black|white]listed-appApp may (or may not) run as systemuserdefault-enabled-vr-appDefault VR Apps component-overrideEnabled component overrides backup-transport-whitelisted-servicePermitted backup transport service components disabled-until-used-preinstalled
-carrier[-associated]-appDisabled apps [privapp/oem]-permissionsAssign extra permissions hidden-api-whitelisted-appNon-platform apps allowed access to full private API allow-associationAllow targetpackage to interact withallowedpackageapp-data-isolation-whitelisted-appApps enabled for data isolation bugreport-whitelistedAllow packageto generate bug reportinstall-in-user-typeInstall packageinuser-type(FULL/PROFILE)named-actorNamed actors (used by Overlay service, q.v. II/3) overlay-config-signaturePackage capable of validating config_signaturefor overlays (q.v. II/3)rollback-whitelisted-appApps eligible for enabling rollback whitelisted-staged-installerInstallers allowed to commit staged install (II/2)
Google documents the
IPowerStats.hal in the Source
site[psh], and its AIDL is similar. The implementation of
the service for Pixel devices
(android.hardware.power.stats@1.0-service.pixel) can be found
in
open source.[psp] Rails data is collected from
| Entity | Provider path |
|---|---|
| RPM
(APSS/MPSS/ADSP/ CDSP/SLPI/SLPI_ISLAND) | |
| SoC | |
| WLAN | |
| Pixel Visual Core (AirBrush) | |
| NFC | |
| GPU | |
| Oslo | IAXXX_SENSOR_MODE_STATS ioctl(2)) |
| IAXXX | IAXXX_POWER_STATS_COUNT ioctl(2)) |
| Citadel (Titan M) | AIDL to Citadel service |
- Preface:
- BTC is down to
$38k$50k$47k$55k$66k. Sheesh - Added a GREAT tip for starting ADB with env/startup options specified for
shell - Thanks to @KingOfPhp:
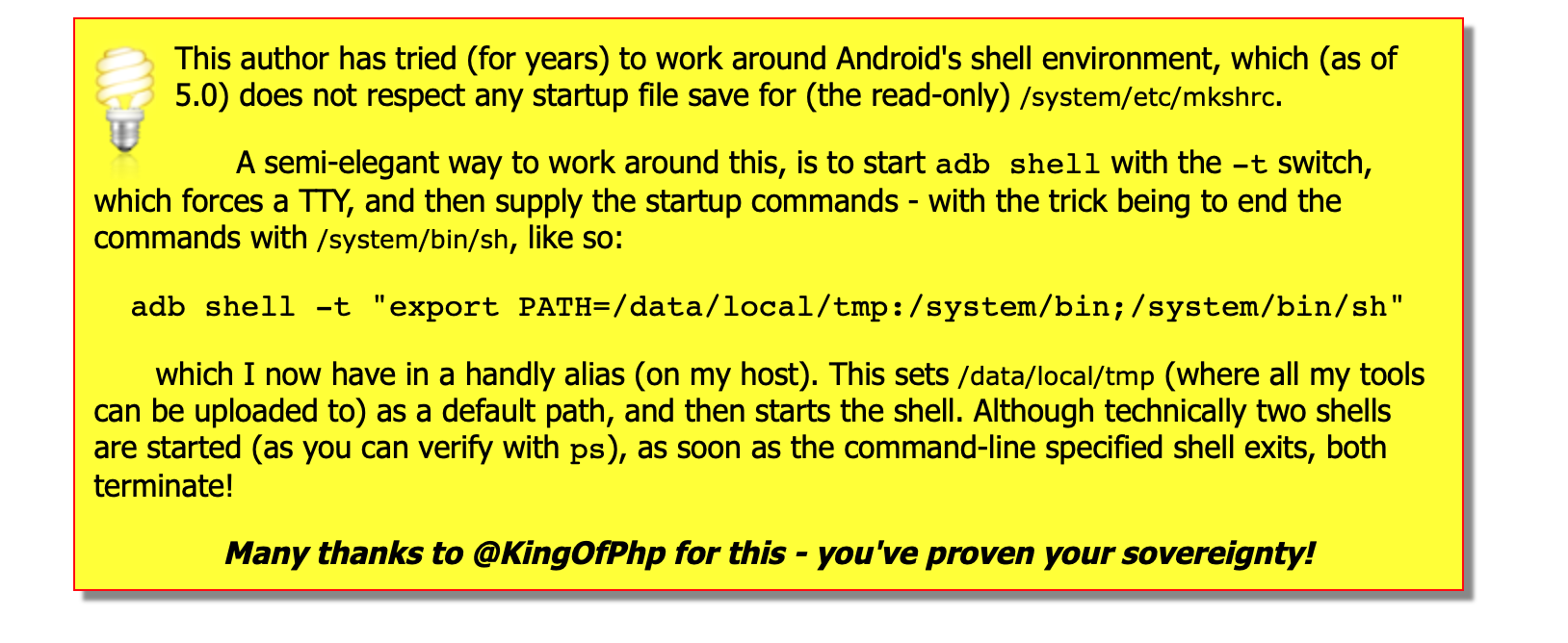
- BTC is down to
- Chapter 1:
- Added note: Bionic is also used outside Android (notably in the hardened GrapheneOS), though Fuchsia's libc is derived from musl[musl].
- Updated Figure 1-3/10 to reflect cases where HIDL server doesn't access
hardware directly, but rather through yet another vendor daemon (very popular,
and I discuss it in II/8, but somehow illustration didn't reflect it). So now
it looks like this:
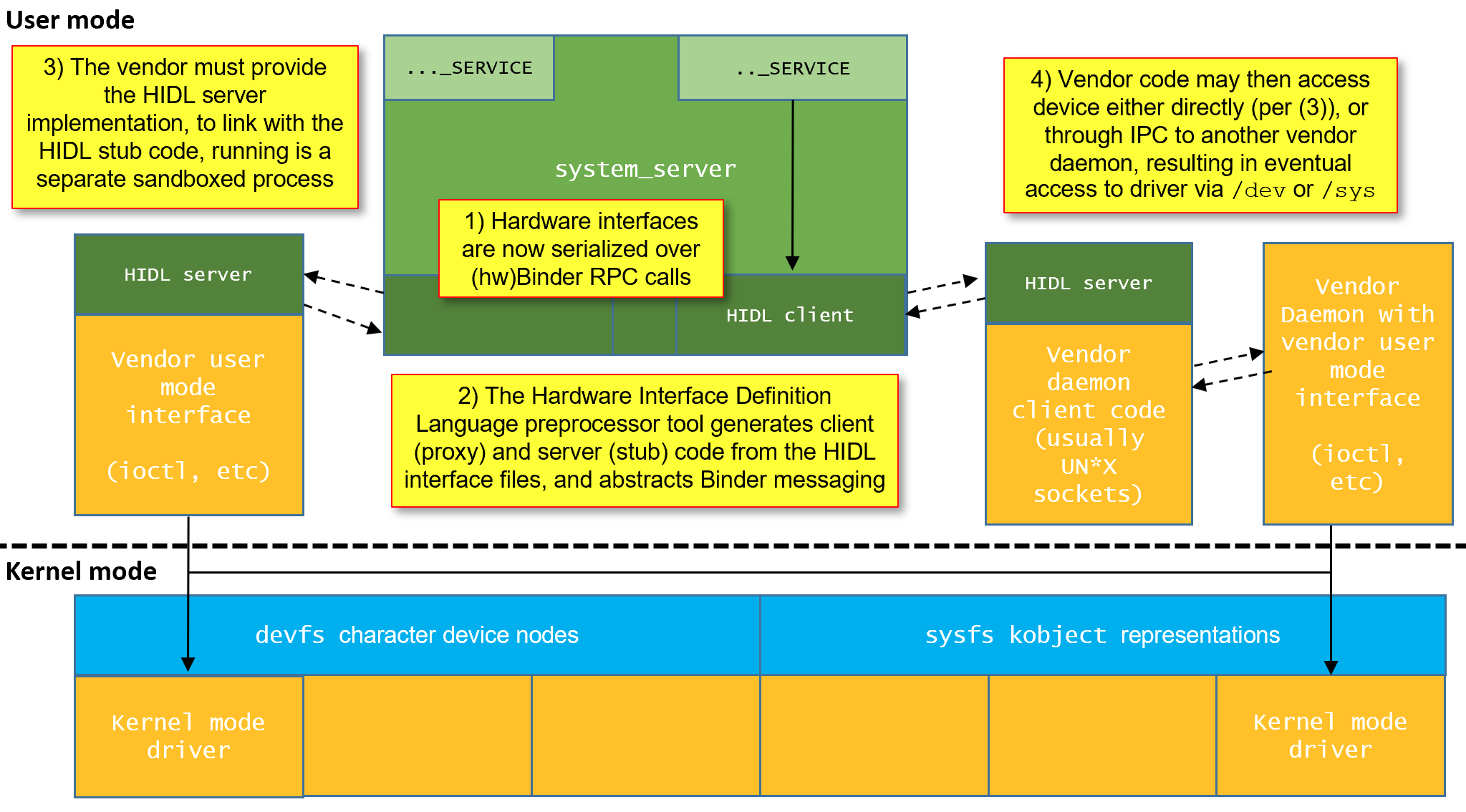
- Chapter 2:
- Updated Table 2/1-1 for ARMv9 launch (happened after v2.0.1 came out...)
v9 A510, A710 Confidential Compute Architecture (CCA), SVE2, Transactional Memory Extension (TME) - Updated Mediatek chipset table: Dimensity 1000 is UFS 2.2,
1200 is UFS 3.1 and now has Realme devices:
Dimensity 1000/L/+ (MT6887/9) CPU: 4xA77@2.6Ghz + 4xA55@2.2Ghz
GPU: ARM Mali-G77 MC9@800Mhz (UFS 2.2)
6-core APU 3.0Oppo Reno3 5G,
Vivo IQOO Z1 5GDimensity 1200 (MT6893) CPU: 1x A78 3x A77@2.6Ghz + 4xA55@2.2Ghz
GPU: ARM Mali-G77 MC9@800Mhz (UFS 3.1)
6-core APU 3.0Realme GT Neo, X9 Pro - Update Samsung Chipset table with Pixel 6[XL]
- Updated Table 2/1-1 for ARMv9 launch (happened after v2.0.1 came out...)
- Also adding
/dev/rpmsg_ctrl#- for Linux Remote Processor Messaging, used by QCom - 2/4.1.1 - Google Devices (up to but not including Pixel 6) use Qualcomm Chipsets
- Added footnote for Huawei -
* - The US imposed ban, along with a worldwide chip shortage in 2021, continue to take its toll on Huawei - it's P50 line of phones not only uses the Qualcomm SnapDragon 888 chipset, but further ships without 5G capabilities. The phones ship with HarmonyOS 2.0.
- Android 11 mandates kernels not support
debugfs. Somehow I missed that in the A11 release notes, but learned this the hard way trying to run bindump on a redfin
(Pixel 5), which comes with A11 as stock. This breaks my
bindumptool. - Note that packages.xml is now ABX! (also, @@TODO no <perms> element)
- Added Google's APEX link:
Google maintains a comprehensive list for these "modular system components"[msc] - Changed Table 5/4-1 (Standard directories created by Android on SD-Cards) to an output
- Output 5/1-2: The loop mounts of apexd - added
ls -l /sys/devices(Thanks, Woody!)
Output 5/1-2: The loop mounts of apexd # # filter '@version' entries, differentiating from non-versioned bind mounts # flame:/ $ mount | grep loop | grep @ /dev/block/loop6 on /apex/com.android.cellbroadcast@300900702 type ext4 (ro,dirsync,seclabel,nodev,noatime) .. /dev/block/loop27 on /apex/com.android.os.statsd@300900700 type ext4 (ro,dirsync,seclabel,nodev,noatime) # # The loop-mounted image can be found through the /sys filesystem # (though this requires root) # flame:/ # cat /sys/devices/virtual/block/loop10/loop/backing_file /system/apex/com.google.android.scheduling.apex
- Added a table of the Binder default transactions I had originally set for
Volume II/7 in place of the paragraph listing them (it made sense, now that 11.0 and 12.0 add even more):
Table 9/1-2-b: Default Transaction Codes supported by (almost) all Binder objects Constant Value Default Behavior DUMP_TRANSACTION_DMP(1598311760)Requests full dump of service state to specified fdaccording to optional arguments. Used bydumpsysINTERFACE_TRANSACTION_NTF(1598968902)Requests interface of service object behind handle.
Expects UTF-16 interface name as replySHELL_COMMAND_TRANSACTION_CMD(1598246212)Command interface for /system/bin/cmd SYSPROPS_TRANSACTION_SPR(1599295570)Deprecated: Calls libutils'sreport_sysprop_change()and any property callbacksPING_TRANSACTION_PNG(1599098439)Null transaction ensuring service object is alive. EXTENSION_TRANSACTION_EXT(1598380116)11.0: Pass an extension BBinderfor objectDEBUG_PID_TRANSACTION_PID(1599097156)11.0: Return service's process identifier (i.e. getpid())SET_RPC_CLIENT_TRANSACTION_RPC(1599230019)12.0 (debug builds, #if BINDER_RPC_DEV_SERVERS,) set socket FD - Also emphasized
webview_zygotedoes not randomize its address space relative to otherZygote[64] instances. - Also added a footnote:
* - Using interfaces could ostensibly enable a design in which a single service endpoint could support multiple interfaces or "personalities", though in practice Binder associates a single interface name with an endpoint.
- @TODO: I'll update Output 9/4-4 (Threads of
system_serverfor new service threads in 12 once the dust settles) - Added NativeTombstoneManager to LocalServices table (9/5-4)
(realized I had missed it earlier since it came into 11.0 but I now discuss tombstones now in II/1):
c.a.s.os.NativeTombstoneManager11.0: Manage tombstones and parse protobuf ( .pb ) tombstones (II/1)
people service
- In 2.4 (Task profiles), after 11/2-16:
On kernels which support it,
libprocessgroupalso adjust/proc/pid/timerslack_ns , which helps coalesce task wakeups, conserving battery life. - In lmkd:
The daemon can thus adjust the "killability" of processes based on the activity state, or other factors (background threads, application services, etc). Google describes the considerations in the
ActivityManagerService'sOOMAdjusterdocumentation.[ooma] - Added
performance_hintdetails (IHintSession, etc. anddumpsys performance_hintfrom a Pixel 6)
android.hardware.dumpstate@1.1:IDumpstateDevice.hal is version 1.1- Android 13 , obviously
- Table 1/1-1 updated for September 2022, with statistics from Statista
- Expanded with ARMv8.6/8.7 and ARMv9.x
- Table 2/1-3 now has snapdragon 8 Gen 1. Under ARM Cortex, three rows:
Also made note under ARMv8.3 ARMv8.5 and ARMv8.6 that the first chipsets to support MTE, when enabled in kernel) is the 8Gen1 and Dimensity 9000CPU partCore Type 0xD46 Cortex-A510 0xD47 Cortex-A710 0xD48 Cortex-X2 - Make note of
/vendor/bin/rebalance_interrupts-vendorin Pixel 6 - Note Dimensity 9000 (just announced) and SnapDragon 8 Gen 1. Wen eta Exynos? :-P
| 11.0: Simulate input events with UHID |
Android 12 (practically, 13) adds support for compressed
APEX files[capex], identified by their apex_pubkey, with the
original (i.e. normally archived but otherwise uncompressed) APEX deflated
inside. This aims to reduce the space taken for
binder_calls_stats (erroneously listed as
"…call_stats" and mentioned twice in table..)getSystemAvailableFeatures() AIDL method (which is noted below table)Android 13 changes (ongoing list before I integrate it into next book update:
- ARMv9 devices (SD 8Gen1, and 2022+ chipsets) - can also support
ARMv8.5 MTE. Made note about support in hw and :
Android 13 native devices (late 2022) are expected to offer MTE (through ARMv9, and thus v8.5 compatible chipsets), and AOSP supports setting it through the bootloader,
android:memtagModeManifest tag, andarm64.memtag.process.*properties, as documented by Google [amte] and discussed in III. - Chapter 7: Added, after Listing 7/3-4:
Android 13 extends the
misc_system_space_layoutwith amisc_memtag_message, identifiable by its magic of0x5afefe5a, to provide the ARMv8.5 MTE hint for the OS, as discussed in III. - Chapter 9: Added services to table
- ILogcatManagerService - logcat privileged requests narc safety_center: [android.safetycenter.ISafetyCenterManager] virtualdevice: [android.companion.virtual.IVirtualDeviceManager] (EXCITING! - Either for Vol III or IV, not sure) selection_toolbar: [android.view.selectiontoolbar.ISelectionToolbarManager] ambient_context: snore/cough detection, really???? IGameService... (will go into IV) IAttestationVerification[Manager]Service.aidl (will go into III)
- Chapter 10: Added ISystemConfig to Table 10/3-7:
Table 10/3-7: The methods exposed by the android.os.ISystemConfigAIDLMethod Notes ... ... int[] getSystemPermissionUids(perm)12.0: Get UIDs holding perm ListgetEnabledComponentOverrides(pkgName) 13.0: Get enabled component overrides (in pkgName) - Chapter 11: Added description of the
tare("The Android Resource Economy") service with dumpsys and link to very detailed README.md in sources - Chapter 12:
ILogcatManagerServicedetail (too long to list here)
| Chapter | Updates | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Chapter 2 |
| ||||||||||||||
| Chapter 10 |
|
MTE is supported by Bionic as of 12. As v2.2 of this book goes to print, Android 13 makes MTE support formal, adding it as a bootloader provided option and/or configurable system property. This remarkably not only catches up with Apple Silicon (which adopted ARMv8.3 PAC three years earlier), but also leaves it behind, as iOS18 on the latest Apple chipset (A18) does not use MTE (although likely does support it, and AAPL chooses to disable it).

- Added
netbpfload.rc (TBD in Vol IV) - Added
misctrl.rc (expanded misc listing 3/2-9-b) - Added
kcmdlinectl.rc (to read from misc under MISC_KCMDLINE_MESSAGE_VERSION)
ProfilingManager)3.4 The ProfilingManager service (Android 15)
| As Of: | Android 15.0 |
| Started by: | SystemServer.startOtherServices() |
| Interface: | a.os.IProfilingService |
| Manager: | a.os.ProfilingManager
|
| Implementation: | a.os.profiling.ProfilingService |
| Directory: | |
| Binaries: | |
| APEX: |
The AIDL presently consists of five methods, which the Manager object and re-exports. The five methods are:
| Method | Purpose |
|---|---|
requestProfiling(profilingType, params,
filePath, tag, keyMostSigBits, keyLeastSigBits,
packageName) | Initiate Profiling |
registerResultsCallback(isGeneralCallback,
callback) | Register a callback. General callbacks are registered via Manager. |
generalListenerAdded() | Notification by Manager to service |
requestCancel(keyMostSigBits,
keyLeastSigBits) | Called by Manager upon CancellationSignal object trigger |
receiveFileDescriptor(fileDescriptor,
keyMostSigBits, keyLeastSigBits) | Retrieve file descriptor with results of profiling |
but the Manager sugarcoats requestProfiling to add an
executor, cancellationSignal, and listener. Applications
are expected to call the Manager's requestProfiling(…)
specifying one the currently supported profilingTypes
PROFILING_TYPE_* constants: …HEAP_PROFILE,
…_JAVA_HEAP_DUMP, …_STACK_SAMPLING and
…_SYSTEM_TRACE. The cancellationSignal allows the
app to abort a profiling session, and the listener is passed in a call
to registerResultsCallback(…).
handleTraceResult(…) calls on
Runnable - calls checkRedactionStatus(…). The
same rescheduling logic applies, until the redaction process times out or
completes successfully. If the latter occurs,
beginMoveFileToAppStorage(…) moves the trace file from the
Throughout all this lifecycle, the registered listener is a
Consumer<ProfilingResult> may be called (through the
Manager) to process any error conditions. On success, and once the file is
moved to the app directory, the app can use the listener's
getResultFilePath() to obtain the file path.
- New Binaries : trace_redactor, mm_events (script) mini-keyctl, preopt2cachename, printflags,sfdo,vintf, ethtool, ldd, otapreopt_slot (script)
- New toy: rtcwake.. losetup, flock, maybe others
- Cover: Genealogy updated to include horses (Pixel 10 models). Front Cover lower bar has Android holding Baklava. Back Cover updated accordingly.
- Chapter 1: Updated for Android 16 stats (surprisingly, already at 7%!), and very few version features.
- Chapter 5:
- Android's
toyboxalso includes theblkdiscardtoy, for "permanetly (sic.) deleting data" - That's not my typo over there, so no need to report it :-)
- Android's
- Chapter 6: Added the 64-bit Linux kernel load address (which was somehow omitted)
- Chapter 8: init adds
swapoff, removesremount_userdata. - Chapter 12:
- Removed
IAtraceDevice.halsince it's been removed from Android.
- Removed